System Security
- Version 69
- Version 70
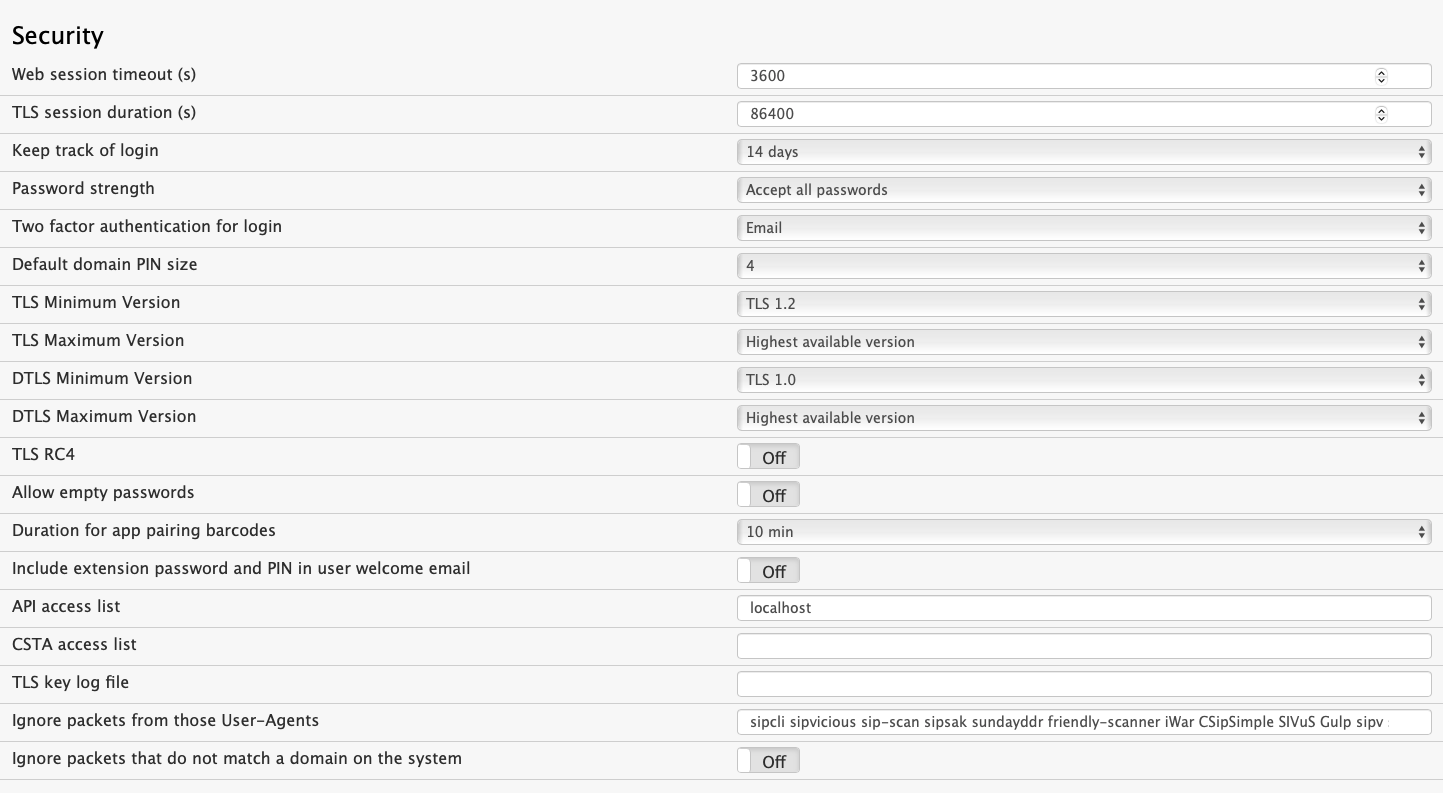
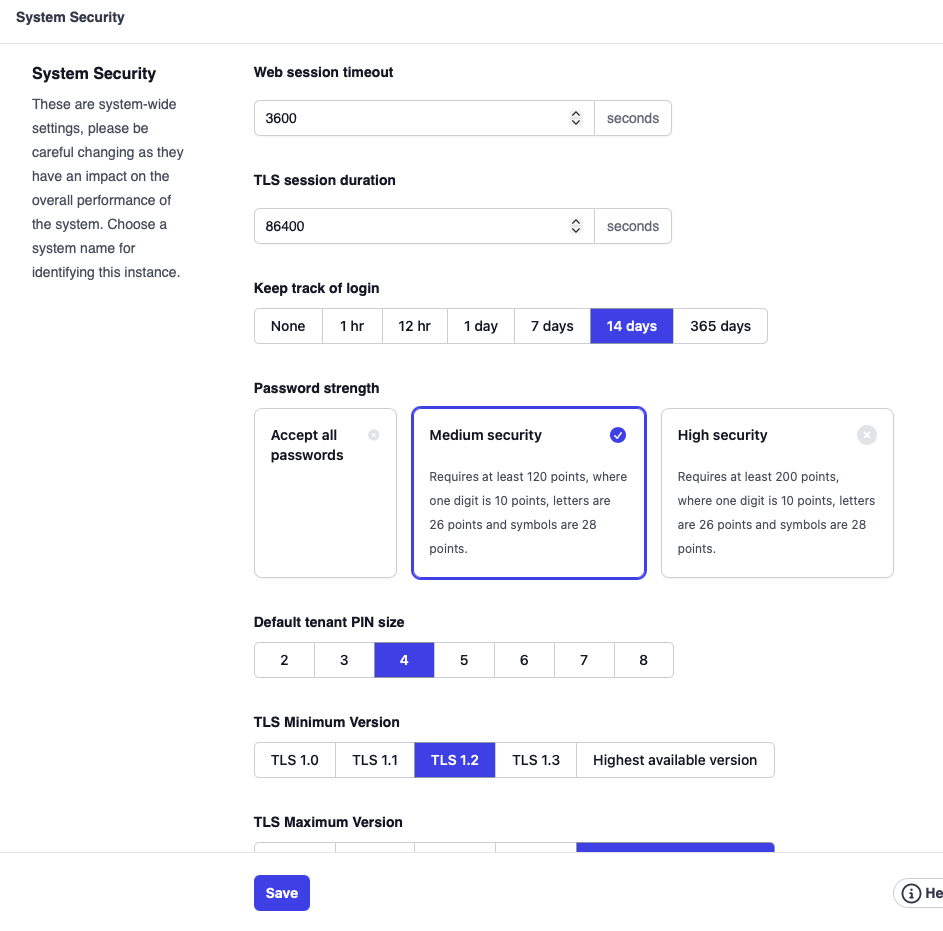
Web Session Timeout: This field determines the length of time a web session will stay active before it times out. The duration is set in seconds, and the default value is 3600 seconds (1 hour). Increase or decrease this setting depending on whether you want the system to log you off after a certain period of time.
TLS session duration: This setting defines how long the TLS session should be kept in the system. When the client and the server keep the session, setting up a new TLS connection is much faster than negotiating a new session from scratch.
Login token validity duration: This setting controls how long login tokens are valid. The default is 30 days.
Keep track of login: The system keeps a log of administrator logins. This setting controls how long the history will be. The default is 14 days.
Password strength: This field is used to specify the types of passwords that are acceptable. The default is "Accept All Passwords," but it is advisable to require medium or high-security passwords. Users should be encouraged to avoid passwords that are dictionary words and to instead create passwords that are more challenging. Medium security requires a score of 120 or higher, high security a score of 200 or higher. A combination of letters, digits, and symbols is recommended. The following table shows the points for characters in the password:
| Character Type | Points |
|---|---|
| Digits | 10 |
| Upper/lowercase letters | 26 |
| Symbols | 28 |
Default tenant PIN size: If there is no PIN size set within the tenant, this setting will be used.
TLS Minimum Version: This field defines the minimum allowed version for TLS. It affects all TLS connections except the UDP-based DTLS (see below), including HTTPS and SIPS.
For most modern equiment, the minimum TLS version should be set to 1.2. Only whne using old equipment that cannot be upgraded any more, lower versions should be used. Using TLS version 1.0 and 1.1 might cause problems with the apps.
TLS Maximum Version: As with the minimum version, the system can also limit the maximum TLS version. This can make sense for compatibility reasons; however generally it makes sense to allow the highest available version.
DTLS Minimum Version: As with the previous setting, this restricts what TLS version is used, however if affects DTLS which is used for RTP key negotiation.
DTLS Maximum Version: As with the previous setting, this restricts what TLS version is used.
TLS RC4: The RC4 cipher is today considered insecure. It is recommended that RC4 stays disabled. However older VoIP phones need this cipher in order to be able to use TLS.
Allow empty passwords: By default every extension on the system must have a password. However some devices are not able to provide a password, then this setting needs to be turned on. Obviously it is strongly recommended to keep this setting turned off.
Duration for app pairing barcodes: The barcodes for pairing the apps with the system contain a token that will expire after a certain time. This settings will determine the duration. A shorter duration is more secure, and a longer duration is more convenient. The expiry can be turned off, which means that the system will use the users password in a hashed format that will not expire. Changing the users password will break the pairing.
Include extension password and PIN in user welcome email: The user's password and mailbox PIN can be generated and emailed to them in the welcome email. This is more convenient however it implies exposing this potentially critical information.
API access list (deprecated): The API access list settings control who can access the deprecated XML API without a session as administrator. It contains a list, separated by space characters, that match the incoming request. The match is either done based on the IP address (e.g. 1.2.3.4, 192.168.0.0/16 or localhost) or the Basic authentication of the HTTP request. The basic authentication information is usually in the form "username:password", but can actually be anything that is sent in the "Basic" authentication header of the HTTP request. This makes it easier to access the server from locations with changing IP addresses. The settings was called "SOAP Trusted IP" in older versions.
CSTA access list: Some CSTA clients are not able to log in to the PBX using the "StartApplicationSession" method. Those clients can be authenticated based on the IP address where they are coming from. The CSTA access list uses the format user@domain:adr. The username must be an existing account in the domain. The address must be a IPv4 or IPv6 address that the PBX perceives on an incoming call. The CSTA messages themselves need to contain the 8-byte header that includes the version number and the XML length, followed by the CSTA message in XML format.
TLS key log file: When tracing packets with Wireshark or other PCAP-based tools, the PBX can write the master key into a key log file. In Wireshark, this file can be set in Preferences→Protocols→SSL→(Pre)-Master-Secret log filename.
Ignore packets from those User-Agents: Network scanners are often using certain names in their User-Agent string. This setting tells the PBX which of those scanners should be ignored. Because the scanner will not receive any traffic back, it will likely give up on scanning. Although this does not avoid the problem of scanning in general, it helps to reduce the load on the system caused by scanners. The list is separated by space characters, starting with version 5.3.3 the system also accepts quoted user agents like "SIP Call", so that the user agent string may contain spaces.
Ignore packets that do not match a domain on the system: When scanning the network, scanners must not only guess the right IP address. In multi-tenant systems, they must also guess the right domain name. This setting helps to keep unauthorized traffic off the system. If this setting is turned on, requests that do not contain a local domain name are ignored, unless the name localhost is used on the system. Exceptions are when the IP address was white-listed or the IP address belongs to a trunk on the system (since version 5.3).