Second Factor Management
Passkeys are the best way to keep login information secure. However, while passwords are still widely used, second factors help to significantly reduce the risk of unauthenticated access. As a reminder, the main problem with passwords is that they are in many cases chosen by humans, and they are easy to guess. In order to improve the strength of passwords, additional factors are widely used.
Because of this we sort of went backward and added a second factor to the login of the PBX. This is available in version 69.5.4 upwards and works on system administrator, tenant administrator and user level.
There are several second factors available. At this point we support only the time-based one-time password (TOTP) factor. There are several reasons for that:
- This factor is well supported by password managers and easy to use. It takes only an extra second to fill the second factor when using a password manager and it provides a security that is almost as secure as passkeys.
- SMS is also well integrated however it does require a connection to an SMS provider. This is difficult on a global scale and would require that system administrators need to set this up.
- Hardware keys are very secure, however they are not as widely available.
- Email requires several manual steps and that the account has an email address associated with it. The PBX already has an email recovery for those who want to use email and using it for second factor purposes does not make the login procedure safer or faster.
There are several apps available for managing TOTP. This includes the Google Authenticator, Microsoft Authenticator, the MacOS Password app and many more.
Create second factor
Before logging in with the second factor, it needs to be set up by the user that is using it later. Administrators need to navigate to the page where they can change their password (security → login) and there select the tab for used tokens and passkeys. Right now, the add button will only offer the TOTP code; this might offer more choices if the PBX supports other factors in later versions. After clicking on the add button, a pop-up window will show a 2D barcode that can be used by authenticator apps on smart phones.
- Version 69
- Version 70
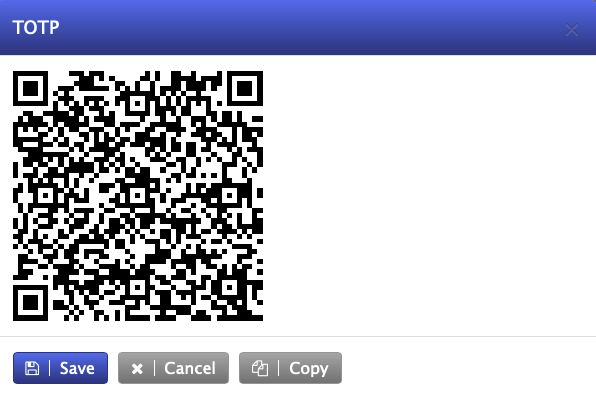
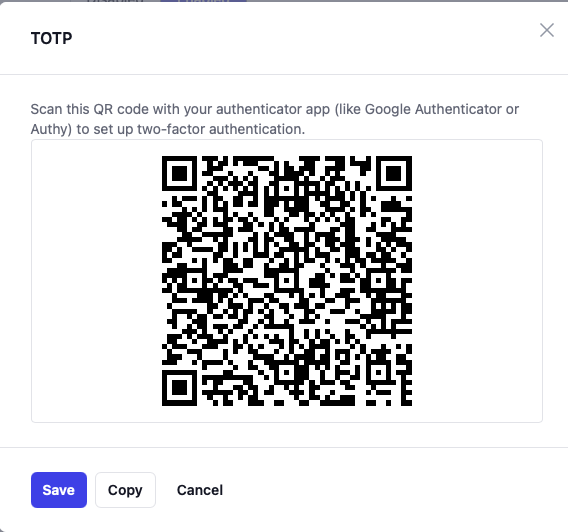
Instead of scanning the code, the TOTP can also be set up by copying the URL with the copy button and then pasting it into the password manager. For example, on Apple this can be done in the Passwords application by selecting the Codes area and then using the New Verification Code to add a new code. This works only if the username and password was previously stored in the Password tool.
![][image2]
The URL copied on the previous screen can be used to set up a new key which will then show a prompt where the username and password needs to be selected. The Codes page will then show the code with the current verification code.
After saving the TOTP code, the list will show the code with a handshake icon. The code does not expire. When deleting the code, the second factor will not be required during login.
- Version 69
- Version 70
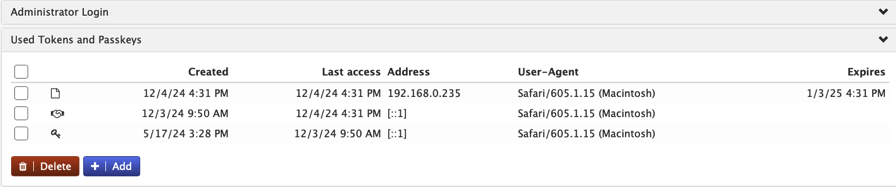
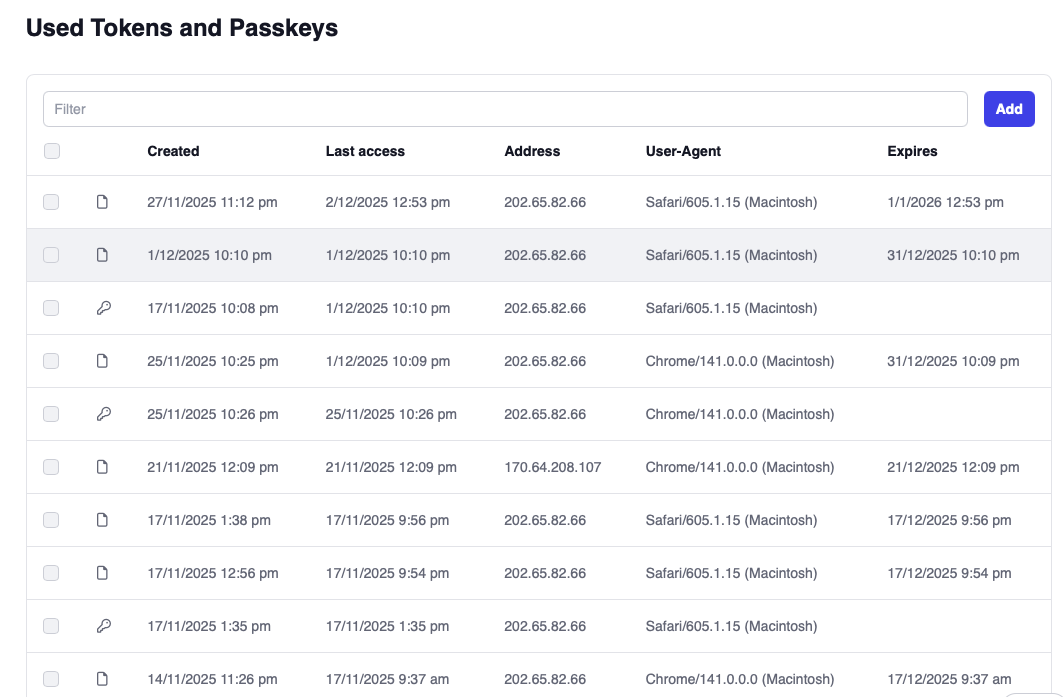
The same procedure can be done on tenant administrator level and also on user level.
Logging in with the second factor
When logging in, you will have to first enter the username and password and press the login button. The PBX backend will then detect that there is a second factor and return that to the login page.
The front will then show the input element for the second factor. The browser offers to fill in the code. This just takes a second.
- Version 69
- Version 70
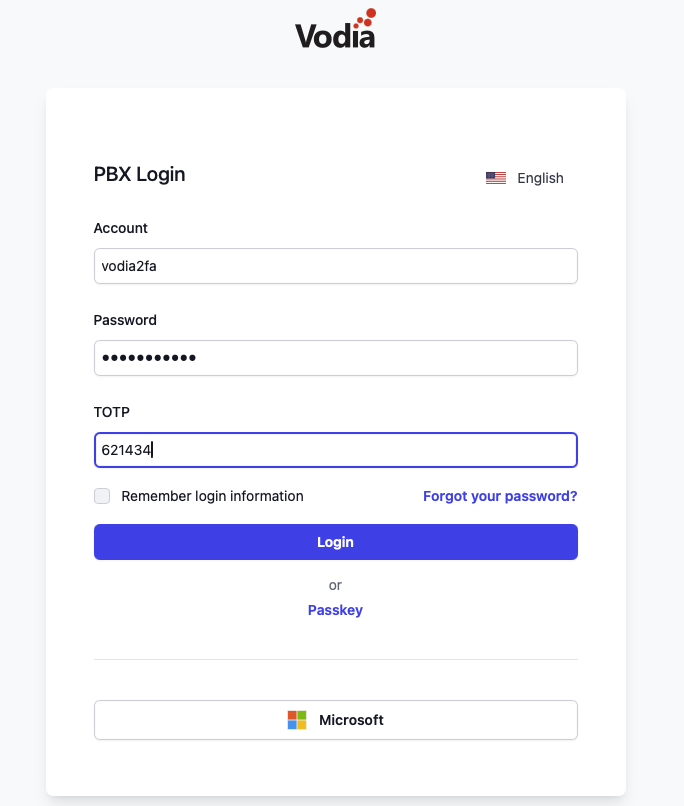
After pressing the login button again, the system will redirect the browser to the page in the PBX portal.
Administrating the second factor
After logging in, users can delete their own second factor in the list of the tokens and passkeys.
Administrators can manage the codes for their users:
- When the super administrator sets a new password for a system administrator account, this will remove the second factor for that account until that administrator sets up a new code.
- When the administrator switches into the user front end, the administrator can delete and create second factors there on behalf of the user.
When using a second factor on an administrator account, that account must login through a session and cannot just use the Basic authentication for the API unless the API was explicitly enabled for that account.